Department of Defense Model of TCP/IP
|
The Department of Defense created TCP/IP to ensure and preserve date integrity. The DoD model is a condensed version of the OSI model and only has four layers.
Defines protocols for node-to-node application communication and also controls user interface specifications. Consists of a set of services that provide ubiquitous access to all types of networks. Applications utilize the services to communicate with other devices and remote applications Protocols and Applications
This layer shields the upper layers from the process of sending data. Also provides an end-to-end connection between two devices during communication by performing sequencing, acknowledgments, checksums, and flow control. Applications using services at this layer can use two different protocols: TCP and UDP. Protocols at the Host-to-Host Layer are:TCP (Transmission Control Protocol)TCP provides a connection-oriented, reliable services to the applications that use its services.
Before data is sent, the transmitting host contacts the receiving host to set up a connection known as a virtual circuit. This makes TCP connection-oriented. During the handshake the two hosts agree upon the amount of information to be sent before an acknowledgment is needed (Windowing). TCP takes the large blocks of data from the upper layers and breaks them up into segments that it numbers and sequences. TCP will the pass the segments to the network layer, which will route them through the Internetwork. The receiving TCP can put the segments back into order. After packets are sent, TCP waits for an acknowledgment from the receiving end of the virtual circuit. If no acknowledgment is received then the sending host will retransmit the segment.
UDP (User Datagram Protocol)UDP transports information that doesn't require reliable delivery; therefore it can have less overhead than TCP as no sequencing or acknowledgments are used. NFS and SNMP use UDP for their sessions, the applications have their own methods to ensure reliability. UDP receives blocks of information from the upper layers, which it breaks into segments. It gives each segment a number, sends it, and then forgets about it. No acknowledgments, no virtual circuits, connectionless protocol.
Differences between TCP and UDP
TCP and UDP Port Numbers TCP and UDP use port numbers to communicate with the upper layers. Port numbers keep track of different sessions across the network. The source port will be above 1024 (unprivileged). 1023 and below (privileged) are known as well known ports and are assigned to common protocols. TCP and upper layer don't use hardware (MAC) and logical (IP) addresses to see the host's address; instead they use port numbers. The Internet Layer exists for routing and providing a single network interface to the upper layers. IP provides the single network interface for the upper layers. Protocols at the Internet Layer are:IP (Internet Protocol)The Internet Protocol (IP) is a network-layer (Layer 3) protocol that contains addressing information and some control information that enables packets to be routed. IP has two primary responsibilities: providing connectionless, best-effort delivery of datagrams through an internetwork; and providing fragmentation and reassembly of datagrams to support data links with different maximum-transmission unit (MTU) sizes. All machines on a TCP/IP network have a unique logical address, an IP address. The Internet Layer (IP) has a complete picture of the entire network and is responsible for path determination and packet switching. IP is the transport for TCP, UDP, and ICMP and provides an unreliable service. It lets the upper layer protocols that use it worry about reliability. IP will perform as a connectionless service because it handles each datagram as an independent entity. IP performs packet switching and path determination by maintaining tables that indicate where to send a packet based on its IP address. IP gets the destination address from the packet. IP receives segments from the Host-to-Host layer and fragments them into packets. IP will then reassemble the packets into segments on the receiving end to send to the Host-to-Host layer. Each packet has the source and destination IP address. Each router will make path determinations based on the destination IP address. ICMP (Internet Control Message Protocol)The Internet Control Message Protocol (ICMP) is a network-layer Internet protocol that provides message packets to report errors and other information regarding IP packet processing back to the source. ICMP utilizes IP to carry the ICMP data within it through a network. ICMP MessagesICMPs generate several kinds of useful messages, including Destination Unreachable, Echo Request and Reply, Redirect, Time Exceeded, and Router Advertisement and Router Solicitation. If an ICMP message cannot be delivered, no second one is generated. This is to avoid an endless flood of ICMP messages. When an ICMP destination-unreachable message is sent by a router, it means that the router is unable to send the package to its final destination. The router then discards the original packet. Destination-unreachable messages include four basic types: network unreachable, host unreachable, protocol unreachable, and port unreachable.
An ICMP echo-request message, which is generated by the ping command, is sent by any host to test node reachability across an internetwork. The ICMP echo-reply message indicates that the node can be successfully reached. PING - Packet Internet Gropher, uses echo message to test physical connectivity. An ICMP Redirect message is sent by the router to the source host to stimulate more efficient routing. The router still forwards the original packet to the destination. ICMP redirects allow host routing tables to remain small because it is necessary to know the address of only one router, even if that router does not provide the best path. Even after receiving an ICMP Redirect message, some devices might continue using the less-efficient route. An ICMP Time-exceeded message is sent by the router if an IP packet's Time-to-Live field (expressed in hops or seconds) reaches zero. The Time-to-Live field prevents packets from continuously circulating the internetwork if the internetwork contains a routing loop. Routers discard packets that have reached their maximum hop count and tell the source machine that the packet is expired. Traceroute - uses ICMP timeouts to find the path a packet takes through the internetwork. ARP (Address Resolution Protocol)Used to find the MAC address from the known IP address. ARP sends a broadcast asking for the machine with the specified IP address to respond with its MAC address. If two devices want to communicate, the first device can send a broadcast ARP message requesting the physical address for a specified IP address. The receiving device responds with its IP address and the first device maintains the entry in its ARP cache. If a device doesn't exist on the same subnet, the sending device addresses the the default gateway's physical address and sends the packet to the default gateway. RARP Reverse Address Resolution Protocol)This protocol is used to find an IP address when the MAC address is known. A machine sends a broadcast with its MAC address and requests its IP address. An example of a device that uses RARP is a diskless workstation. Since it can't store its logical network address, it sends its MAC address to a RARP server to requests its IP address. A RARP server responds to the RARP request with the device's IP address. The Network Access Layer monitors the data exchange between the host and the network. Oversees MAC addressing and defines protocols for the physical transmission of data. 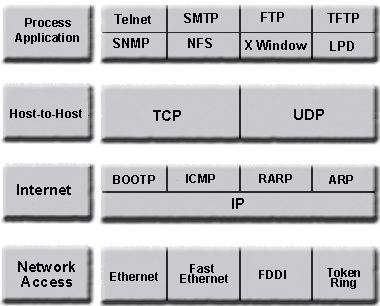 BACK |
||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
